Prologue (Oct 13, 2024)
The deadly attack by Hezbollah on the Golani Brigade base in Israel resulted in the tragic loss of four soldiers and injuries to sixty others. The attack involved Hezbollah deploying a Iran-manufactured Shahed-136 drone, known for its precision strike capabilities and lethal payload. This drone has an operational range of up to 2,500 kilometers and can carry a significant warhead, making it a formidable tool in asymmetric warfare [8]. From an Israeli Air Force (IAF) post-mortem:
The Lebanese terror group fired short-range rockets at the north, three precision rockets toward Haifa, and launched three drones at Israel last night. One of the drones was shot down by the navy, another by the Iron Dome.
The third was pursued by Israeli jets and helicopters, which fired at it twice, according to the IAF investigation. Electronic warfare measures also failed to force the UAV to lose its bearings. It dropped off radars 30 miles (48 kilometers) northeast of Acre, and the IAF assumed that it had crashed.
The IAF investigation into the incident found that the drone appeared back on radars for another minute in the half-hour between its dropping off of screens and the strike, but forces did not identify it as a drone at the time, and therefore did not trigger warning alarms. There are hundreds of objects flying in Israeli airspace just above buildings at any given time, including birds, adding to the challenge of identifying a drone that appears in an unexpected location.
In the wake of the deadly strike, the IAF has also set a goal of completely eliminating Hezbollah’s Unit 127, responsible for its UAV production, maintenance and operation
(Nov 3) : A joint IDF, IAF and the Intelligence Division op eliminated Hezbollah Unit 127 commander Ali Barkhat. Ali Barakat was a significant source of knowledge for Unit 127, spending over a decade planning and carrying out UCAV attacks on Israel, as well as developing cruise missiles.
The proliferation of unmanned combat aerial vehicles (UCAVs), particularly kamikaze drones, introduces a new dimension of threat to modern warfare. Characterized by low cost, precision strike capabilities, and significant psychological impact, these weapons are increasingly recognized as game-changers in military conflicts [2].
"Weaponized drones have absolutely changed the way the game is played" video
PLA and Kamikaze UCAV Warfare
The People's Liberation Army (PLA), with its stated goal of "reunifying" Taiwan with mainland China—potentially through force—has invested heavily in developing and deploying various UCAVs, including kamikaze drones. This note addresses the urgent need to understand the strategic and tactical implications of this evolving technology. It provides a comprehensive assessment of the PLA's kamikaze drone arsenal, explores potential invasion scenarios, and identifies vulnerabilities and countermeasures.
1. Introduction
The possibility of a PLA invasion of Taiwan remains a focal point of geopolitical tension. While conventional military assessments often dominate discussions, the increasing role of asymmetric warfare, particularly through unmanned combat aerial vehicles (UCAVs), demands focused analysis. Kamikaze drones, a specific class of UCAVs, possess unique capabilities that could significantly alter the dynamics of a cross-strait conflict. This paper examines the strategic and tactical implications of these weapons in a Taiwan invasion scenario, incorporating technical specifications, geographical considerations, and recent research insights.
2. Kamikaze Drones: An Asymmetrical Advantage
Kamikaze drones possess characteristics that make them particularly suited for asymmetric warfare. Their cost-effectiveness allows for mass production and deployment, enabling saturation attacks and swarm tactics. Modern guidance systems, including GNSS and inertial navigation, coupled with advanced target recognition algorithms, allow for precise targeting even in GPS-denied environments. The psychological impact of drone swarms can profoundly affect both military personnel and civilian populations, potentially impacting morale and eroding public support for conflict [6]. Furthermore, kamikaze drones can be readily adapted for various missions, including anti-ship, anti-tank, suppression of enemy air defenses (SEAD), and the destruction of critical infrastructure.
These attributes render kamikaze drones a potent tool for actors seeking to offset conventional military disadvantages.
3. Taiwan's Eastern Flank: A Geographic Vulnerability
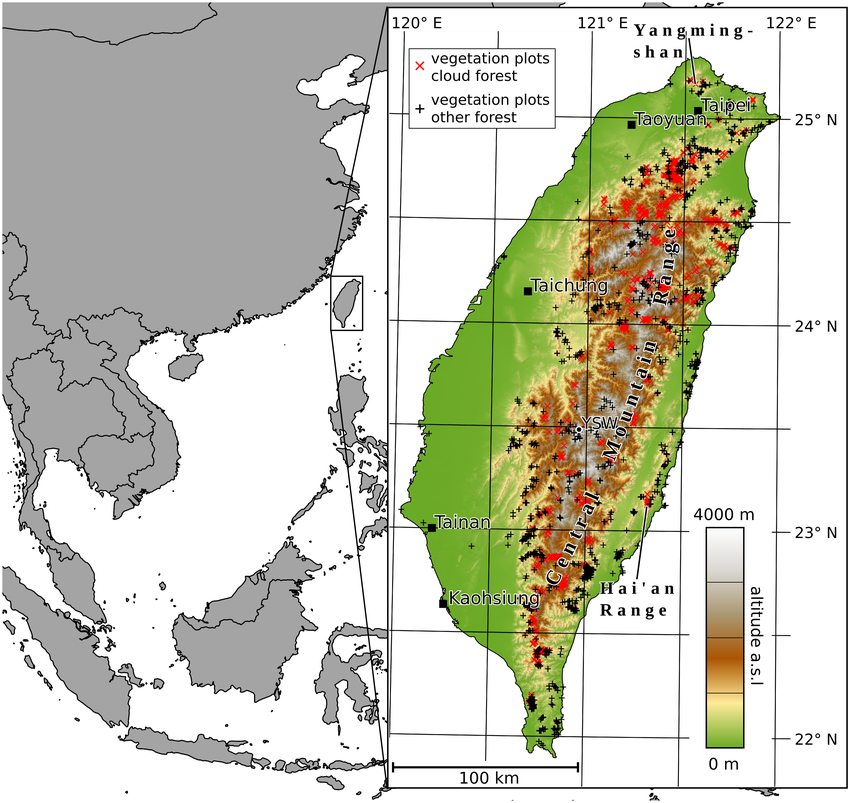
Taiwan's western coast is heavily fortified, presenting a significant obstacle to a direct amphibious assault. However, its eastern coast, characterized by rugged terrain, fewer major cities, and a less concentrated military presence, offers a potential avenue for an asymmetric attack leveraging kamikaze drones.
The Central Mountain Range limits access points and hinders rapid deployment of reinforcements while offering concealment and potential launch positions for drone attacks. The limited infrastructure on the east coast, with fewer major ports and airfields compared to the west, restricts Taiwan's ability to quickly deploy reinforcements or launch counter-offensives. The sparse population on the east coast, while potentially minimizing civilian casualties, also presents challenges for local defense mobilization.
Lukács' Fog of War
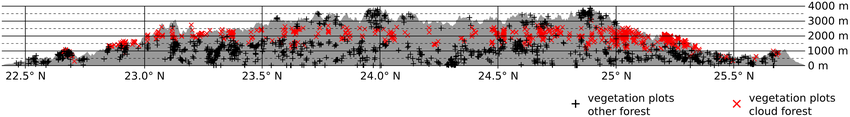
Schulz et al. [11] presents a detailed analysis of the distribution of montane cloud forests (MCF) in Taiwan, utilizing 12 years of MODIS-derived ground fog frequency data. The study highlights the strong correlation between the occurrence of MCF and high ground fog frequency, particularly at altitudes between 1500 and 2500 meters above sea level.
The winter monsoon creates heavy fog conditions on the windward slopes of the Central Mountain Range (CMR), offering the PLA a strategic advantage by providing cover for troop movements and drone launches. The Massenerhebung effect, which lowers vegetation zones in isolated mountain areas, further complicates the operational landscape by creating pockets of dense fog at lower altitudes. These areas, particularly in the northern and southern regions of the CMR, could serve as strategic launch sites for UCAVs, enabling the PLA to bypass higher-altitude defenses and strike critical infrastructure in valleys or along Taiwan's eastern coast.
Given the potential impact of fog on EO/IR sensors, the PLA might prioritize drone platforms that incorporate sensor fusion (e.g., combining EO/IR with radar or LiDAR) or utilize alternative guidance systems, such as terrain-following radar or inertial navigation, to maintain operational effectiveness in fog-prone environments. This is especially pertinent for PLA drone platforms like the CH-901/GJ-2 and GJ-1/WS-43, which rely heavily on electro-optical/infrared (EO/IR) sensors for navigation and target acquisition.
4. PLA's UCAV Arsenal and Potential Tactics
The PLA has actively developed and deployed a range of UCAVs, including platforms well-suited for kamikaze missions. Based on observed deployments and expert analysis, one can extrapolate capabilities w reasonable likelihood.
Technical Specifications of PLA UCAVs
| Platform | Type | Range (km) | Payload (kg) | Propulsion | Guidance | Key Features/Capabilities | Potential Vulnerabilities |
|---|---|---|---|---|---|---|---|
| CH-901/GJ-2 | Long-range loitering munition | 1500 | 50 | Piston engine | GPS/GNSS, inertial navigation | Standoff strikes, deep strike missions, swarm tactics, modular warheads | GPS spoofing/jamming, communication interception, limited maneuverability |
| ASN-301 | Anti-radiation loitering munition | 150 | Anti-radiation warhead | Electric motor | Passive radar homing | SEAD missions, passive homing, long loiter time | Decoy emitters, electronic countermeasures (ECCM) |
| GJ-1/WS-43 | Reconnaissance and strike drone | 250+ | ~10 | Electric motor | GPS/GNSS, inertial navigation | Reconnaissance, precision strikes, swarm tactics | Limited range, limited payload |
| Divine Eagle | High-altitude, long-endurance (HALE) UAV | N/A (Global) | N/A (Surveillance, EW, potential drone carrier) | Jet engines | Autonomous, potentially satellite-guided | Persistent surveillance, electronic warfare, potential drone carrier | High-altitude interception, satellite tracking |
It should be noted that the PLA's emphasis on networked warfare (e.g., SoSOM see Appendix) will significantly enhance the coordination and lethality of its drone swarms.
These platforms can be employed in various tactical scenarios, including swarm attacks to overwhelm defenses, SEAD missions that integrate electronic warfare support, and anti-ship tactics to target naval vessels. The PLA could leverage networked communication systems and distributed AI algorithms for coordinated swarm attacks, complicating interception efforts against large numbers of drones converging on critical targets.
5. Exploiting Taiwan's Eastern Flank
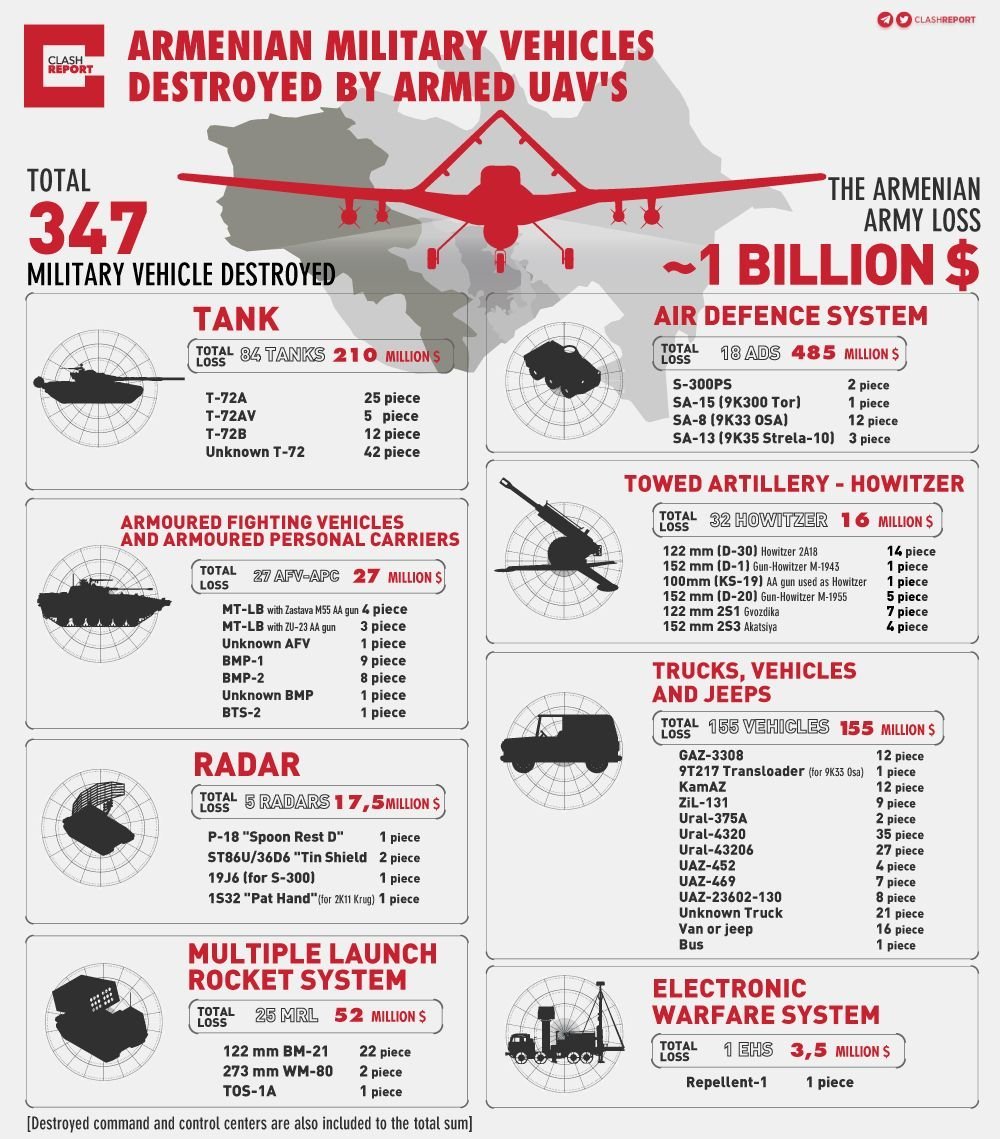
Taiwan's eastern defenses, being less fortified than those on the western coast, present a potential vulnerability that the PLA could exploit using kamikaze drones. The CSIS wargame offers insights into the dynamics of such a scenario, emphasizing the potential for swarm attacks. A swarm of 200-300 CH-901/GJ-2 drones could effectively saturate Taiwan's eastern air defenses, prioritizing key targets like air defense radar sites, air bases, command and control centers, and port facilities.
To further confuse Taiwan's defenses, the PLA could deploy drone decoys alongside electronic warfare tactics. Low-cost, expendable drones designed to mimic larger aircraft could trigger air defense responses, while advanced jamming techniques could disrupt radar and communication systems [4].
Additionally, psychological operations could exploit the fear generated by drone swarms. Propaganda payloads could be used to demoralize the population, while social media could amplify the psychological impact of drone attacks, influencing public opinion and pressuring the government to make concessions [3].
The PLA could also deploy swarms of GJ-1/WS-43 drones to target Taiwanese naval vessels. With their high speed and maneuverability, these drones would be difficult to intercept, potentially crippling Taiwan's ability to respond to an amphibious assault. Furthermore, the PLA might utilize autonomous drone submarines to target undersea infrastructure, disrupting logistics and creating confusion.
| Platform | Warhead Type | Tactical Scenarios |
|---|---|---|
| CH-901/GJ-2 | High-explosive fragmentation, potentially thermobaric | * Saturation attacks on air defenses, airbases, command centers, and critical infrastructure. * Standoff strikes against high-value targets. * Reconnaissance and target acquisition for artillery or missile strikes. |
| ASN-301 | Specialized anti-radiation warhead designed to disable radar systems. | * Suppression of enemy air defenses (SEAD). * Targeting of enemy radar installations and early warning systems. * Disruption of enemy command and control networks. |
| GJ-1/WS-43 | High-explosive fragmentation, potentially armor-piercing | * Swarm attacks on naval vessels. * Precision strikes against time-sensitive targets. * Close air support for ground troops. |
| Divine Eagle | Not typically armed with conventional warheads. May carry electronic warfare payloads or act as a mothership for smaller kamikaze drones. | * Long-endurance surveillance and reconnaissance. * Communications relay and electronic warfare support. * Potential for launching smaller kamikaze drones. |
6. A Sobering Assessment: A New Era of Warfare
CSIS Wargame Insights
The 2023 CSIS wargame simulated a Chinese amphibious invasion of Taiwan, incorporating players from the US, China, Taiwan, and Japan. Conducted 24 times, this exercise varied key assumptions about political decisions, military capabilities, and rules of engagement, yielding sobering results for the US and its allies.
Among the most striking findings was the significant loss of ships, aircraft, and personnel, even in scenarios where the invasion was ultimately repelled. The wargame highlighted the vulnerability of surface vessels to missile attacks, particularly from Chinese anti-ship ballistic missiles (ASBMs) and long-range anti-ship cruise missiles (ASCMs). This vulnerability raises critical questions about the effectiveness of naval defenses in a potential conflict.
Access to US bases in Japan emerged as a crucial factor in the defense of Taiwan. Without these bases, US fighter aircraft and bombers would need to operate from more distant locations, which would diminish their effectiveness and increase their vulnerability. The logistical challenges of sustaining military operations were underscored throughout the wargame. Taiwan's geographic isolation complicates the reinforcement of the island once hostilities commence, underscoring the urgent need for prepositioning critical supplies and equipment.
These insights reveal the formidable challenges of defending Taiwan against a determined PLA invasion, even with US intervention. The wargame's emphasis on the vulnerability of surface ships and the critical role of air bases in Japan directly informs the potential tactical applications of kamikaze drones discussed in this analysis.
RAND Air Combat Study: Lessons for the UCAV Age
The 2008 RAND study, Air Combat Past, Present and Future, provides valuable insights into the evolving nature of air combat and the complexities of achieving air superiority in a contested environment. Although the study predates the widespread use of kamikaze drones, its analysis remains relevant in understanding their potential role in a Taiwan conflict.
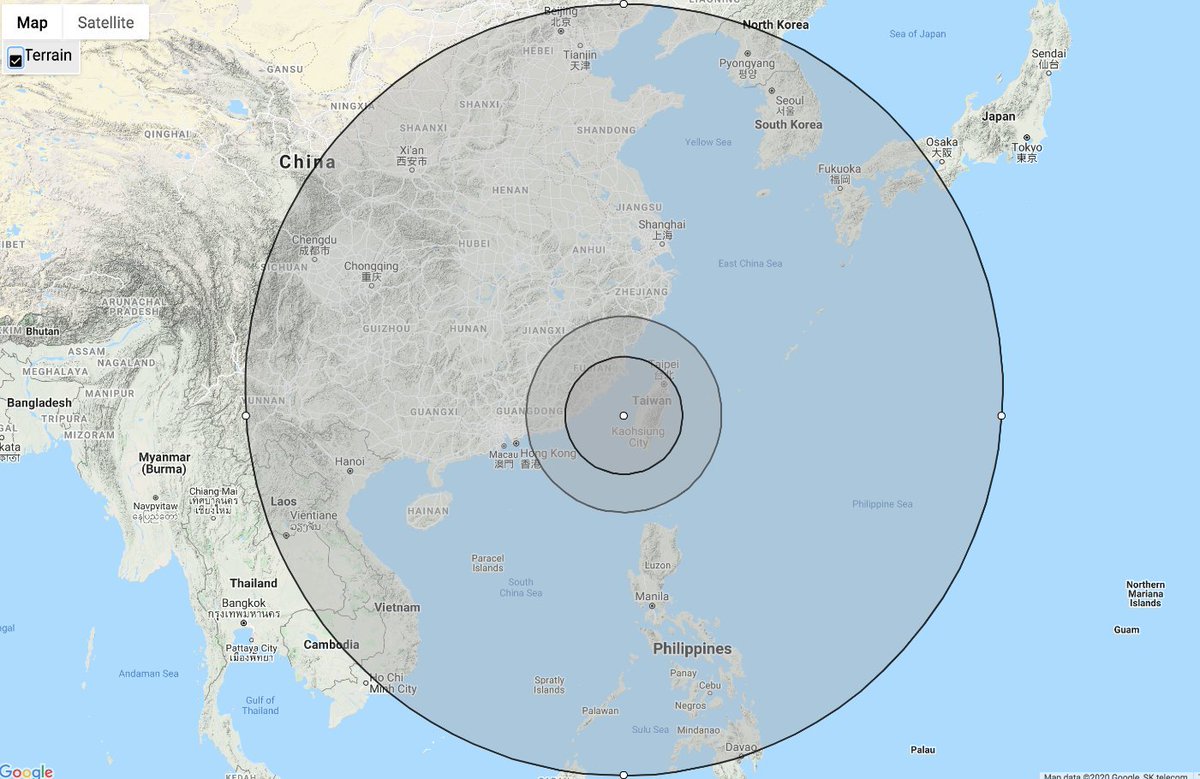
One of the key takeaways from the RAND study is the vulnerability of air bases to missile attacks, particularly in the Western Pacific, where US bases are within range of Chinese ballistic and cruise missiles. This vulnerability underscores the PLA's potential to disrupt US airpower by targeting bases in Japan and Guam, especially using kamikaze drones to target critical infrastructure.
Moreover, the study emphasizes the importance of electronic warfare (EW) in modern air combat. As the PLA invests in EW capabilities—including jamming, spoofing, and deception technologies—it could significantly degrade the effectiveness of US and Taiwanese airpower. This capability creates opportunities for kamikaze drone attacks, leveraging the chaos wrought by electronic warfare to launch precise assaults.
The concept of attrition warfare discussed in the RAND study is also pertinent. It highlights the strategy of gradually wearing down an enemy's forces through sustained combat. Kamikaze drones, with their low cost and capacity for inflicting significant damage, could be effectively employed in such a strategy, overwhelming defenses through sheer numbers and relentless attacks.
Amateurs talk about strategy, professionals talk about logistics.
References
[1] Center for Strategic and International Studies (CSIS). (2023). The First Battle of the Next War: Wargaming a Chinese Invasion of Taiwan.
[2] Demirel, A. R., Yavuz, M. M., & Tokgöz, N. (2024). Modeling and Analysis of Kamikaze UAV Design with 3 Different Wing Configurations. Journal of Mathematical Sciences and Modelling, 7(2), 90-111.
[3] Mansoor, W., et al. (2023). A Comprehensive Review of Recent Research Trends on Unmanned Aerial Vehicles (UAVs). Systems, 11(8), 400.
[4] Nash, D. R. (2024). UAV Drone Security of Control for Increased Safety-of-flight. [Doctoral dissertation, Dakota State University].
[5] Osmani, K., & Schulz, D. (2024). Comprehensive Investigation of Unmanned Aerial Vehicles (UAVs): An In-Depth Analysis of Avionics Systems. Sensors, 24(10), 3064.
[6] Yang, Y., et al. (2024). Advancement Challenges in UAV Swarm Formation Control: A Comprehensive Review. Drones, 8(7), 320.
[7] RAND Corporation. (2008). Air Combat: Past, Present, and Future.
[8] Zampronha, D., & Albuquerque, A. (2024). Cheaper Precision Weapons: An Exploratory Study about the HESA Shahed 136. Advances in Aerospace Science and Technology, 9(1), 40-59.
[9] Yang, J., et al. (2024). Deep Learning for Target Recognition and Classification in Unmanned Aerial Vehicles. IEEE Transactions on Aerospace and Electronic Systems.
[10] Liang, F., & Xiangsui, Y. (1999). Unrestricted Warfare. People's Liberation Army Literature and Arts Publishing House.
[11] Schulz, H. M., Li, C.-F., Thies, B., Chang, S.-C., & Bendix, J. (2017). Mapping the montane cloud forest of Taiwan using 12 year MODIS-derived ground fog frequency data. PLOS ONE, 12(2), e0172663.
Appendix
A.1 Networked Warfare: The PLA's SoSOM Doctrine
The People’s Liberation Army (PLA) emphasizes networked warfare through its "System of Systems Operations Management" (SoSOM) doctrine, which is integral to its drone swarm tactics. SoSOM envisions a highly interconnected battlespace where various military assets—including sensors, weapons systems (such as Unmanned Combat Aerial Vehicles, UCAVs), and command centers—operate cohesively through a secure and resilient network. This integration facilitates real-time data sharing, enabling rapid and synchronized responses across multiple units, thereby fostering collaborative targeting and the effective engagement of high-value assets. While specific operational details of SoSOM remain classified, its core principles are evident in PLA writings and exercises [10].
SoSOM enhances operational effectiveness by providing commanders with a dynamic and comprehensive understanding of the battlespace. Data fusion from UCAVs, satellites, and ground-based sensors creates a rich tapestry of situational awareness, informing decision-making at all levels. This shared understanding enables rapid adaptation to evolving conditions, optimizing the use of drone swarms for diverse objectives. The PLA's literature underscores the importance of information dominance and real-time decision-making in modern warfare.
The doctrine prioritizes resilience and redundancy within the network, distributing operational capabilities across multiple nodes to ensure continued functionality even if some elements are compromised. This distributed architecture enhances survivability and enables complex coordinated maneuvers, such as saturating enemy defenses or executing flanking attacks, significantly amplifying operational effectiveness. This aligns with the PLA's focus on asymmetric warfare and exploiting vulnerabilities in adversarial networked systems.
A.2 AI Autonomous Swarms and Enhanced Combat Capabilities
The PLA is rapidly integrating artificial intelligence (AI) into its UCAV development programs, recognizing its transformative potential. AI enhances the autonomy of PLA drones, enabling effective navigation in complex environments. AI-powered systems allow drones to adapt to changing conditions, whether avoiding adverse weather or dynamically adjusting flight paths based on new intelligence [2]. This capability facilitates real-time independent decision-making, reducing reliance on human operators and enabling faster response times.
AI also revolutionizes target recognition capabilities. Advanced algorithms empower drones to differentiate between friendly and enemy forces, identify high-value targets, and minimize collateral damage—an essential consideration in urban or densely populated areas [6]. Leveraging machine learning allows for continuous improvement in target recognition and classification accuracy.
Furthermore, AI is essential for coordinating drone swarms. By enabling communication and cooperation among drones, AI optimizes flight paths and allows for adaptive tactics in response to enemy actions [3]. This dynamic coordination enables swarms to adjust formations, prioritize targets based on real-time assessments, and implement complex maneuvers, significantly complicating defensive measures for adversaries.
The PLA is rapidly integrating artificial intelligence (AI) into its UCAV development programs. AI has the potential to significantly enhance the autonomy, target recognition capabilities, and swarm coordination of PLA drones. For example, AI-powered autopilots could enable drones to navigate complex environments, adapt to changing conditions, and make independent decisions in real-time. AI algorithms can also enhance target recognition, enabling drones to differentiate between friendly and enemy forces, identify high-value targets, and reduce collateral damage. Furthermore, AI can play a crucial role in swarm coordination, enabling drones to communicate and cooperate with each other, optimizing their flight paths, and adapting their tactics in response to enemy actions.
A.3 STRIDE Analysis of PLA UCAV Arsenal
| Threat | UCAV Platform | Vulnerabilities | Subsystems & Implications |
|---|---|---|---|
| Spoofing (S) | CH-901/GJ-2: Reliance on civilian GPS for navigation, coupled with basic BeiDou/inertial systems, makes it highly susceptible to spoofing. Low-cost COTS components likely lack advanced anti-spoofing measures. ASN-301: Its long-endurance mission profile and potential reliance on GPS for mid-course navigation create a critical spoofing vulnerability, potentially disrupting its electronic warfare operations. GJ-1/WS-43: While primarily using BeiDou, any integration of GPS for enhanced precision or redundancy introduces a spoofing risk, potentially jeopardizing its high-speed penetration capabilities. Divine Eagle: Dependence on GPS for extended HALE missions creates a significant spoofing vulnerability, potentially compromising its persistent surveillance capabilities. |
Reliance on unencrypted/easily spoofed civilian-grade GPS. Vulnerability to state-sponsored spoofing. | Navigation systems (BeiDou, GPS, inertial). Lack of advanced anti-spoofing capabilities in COTS components. |
| Tampering (T) | CH-901/GJ-2: Extensive use of COTS components simplifies maintenance and reduces costs but significantly increases vulnerability to tampering and reverse engineering, potentially compromising its tactical reconnaissance mission. ASN-301/GJ-1/Divine Eagle: While likely incorporating more specialized components, reliance on the CASC supply chain introduces potential risks of malicious hardware/software insertion during manufacturing or maintenance. |
Malicious hardware/software insertion potential. Supply chain attack vulnerability. | All subsystems potentially affected. COTS components and centralized manufacturing increase risk. |
| Repudiation (R) | All Platforms: Lack of publicly available information on secure logging and identification mechanisms makes attribution difficult, especially in contested airspace. This ambiguity could be exploited to deny responsibility for drone actions. | Difficulty attributing attacks due to lacking identifiers/secure logging. | Flight control and communication systems. Lack of transparent security protocols. |
| Information Disclosure (I) | GJ-1/WS-43: High-bandwidth datalink, even with encryption, is susceptible to sophisticated interception, potentially exposing valuable SAR and EO/IR sensor data. Divine Eagle: Advanced sensor suite (radar, EO/IR, potential hyperspectral) and reliance on satellite/laser communication links make it a prime target for data exfiltration. Compromised data could reveal critical intelligence. |
Unencrypted or weakly encrypted data links. Interception/eavesdropping vulnerability. | Communication and sensor systems. Data encryption and transmission security protocols. |
| Denial of Service (D) | CH-901/GJ-2: Line-of-sight datalink is highly vulnerable to jamming, potentially disrupting its reconnaissance capabilities. ASN-301/Divine Eagle: Reliance on satellite communication introduces different jamming challenges, requiring specialized electronic warfare capabilities. All Platforms: While BeiDou offers some resilience against GPS jamming, targeted attacks on other navigation systems (inertial, terrain-following radar) could disrupt operations. |
GPS/GNSS jamming susceptibility. C2 link disruption potential. | Communication and navigation systems. Anti-jamming capabilities and redundancy measures. |
| Elevation of Privilege (E) | GJ-1/WS-43/Divine Eagle: Sophisticated flight control systems and potential AI integration for autonomous operations create a complex attack surface for exploitation. Software vulnerabilities could allow unauthorized access and manipulation of critical flight parameters. All Platforms: Cybersecurity vulnerabilities in any subsystem could be exploited to gain elevated privileges and compromise the entire system. |
Flight control/autonomous navigation software vulnerabilities. Remote hijacking/takeover potential. | Flight control, communication, and computing systems. Software security and access control mechanisms. |
postscriptum
Beyond the publicly known GPS and TERCOM, the HF-2E incorporates an advanced inertial navigation system (INS) with potential integration of a celestial navigation system for enhanced accuracy and resistance to jamming. The terminal guidance system uses a dual-mode seeker combining imaging infrared (IIR) and active radar, with sophisticated algorithms for target recognition and discrimination. This allows the missile to engage moving targets and penetrate advanced air defense systems.
≡ 📜🔥 (🧠 ∪ 📚) ∩ (✡️ ∪ 🕎) ∖ (❓ ∪ 🚫) ⟨הלכה⟩ ⇔ ⟨🔄 ⨹ 🗣️⟩ ⊇ ⟨👴 ⨹ ❤️⟩ ⊂ ⟨📝 ⨹ ⚖️⟩ ⊇ ⟨🔄 ⨹ 📚⟩ ⊂ ⟨🕍 ⨹ 🌍⟩ ⊇ ⟨🔄 ⨹ 🙏⟩ 📜🔥
(📜🔥 Créé par HKBH avec dyb comme un récipient reconnaissant, dans la miséricorde 📜🔥)